Mar 12, 2021 How to install telnet into a alpine docker container. This is useful when using the celery remote debugger in a dev environment. Clone via HTTPS Clone with Git. Install Linux Deploy, JuiceSSH, in Linux Deploy install kalilinuxarm (u need the piggy helper and enable the SSH) and type: sudo apt update sudo apt install golang git build-essential libpcap-dev libusb-1.0-0-dev libnetfilter-queue-dev. Install Linux Deploy, JuiceSSH, in Linux Deploy install kalilinuxarm (u need the piggy helper and enable the SSH) and type: sudo apt update sudo apt install golang git build-essential libpcap-dev libusb-1.0-0-dev libnetfilter-queue-dev.
Even if Alpine is designed to run from RAM, it has some similarities in package management with both Gentoo and Debian. This page outlines those similarities and differences, to help Debian and Gentoo users to use Alpine.
The page was originally copied from: http://gentoo-wiki.com/TIP_Converting_from_or_to_Debian
- 1Package management
- 2Runlevel & Initscripts
- 3Config Files
Where Gentoo has portage and emerge; Debian has, among others, apt; Alpine uses apk-tools. This section compares how apk-tools is used, in comparison to apt-get/aptitude and emerge.
Note that Gentoo is source-based, just like ports in FreeBSD are, while Debian uses pre-compiled binaries. Alpine is compiled using Gentoo's portage, but Alpine itself uses its own apk-tools binary package which is more similar to FreeBSD's binary packages.
Updating package database
Gentoo will update the build-from-source scripts and are the updating of the database is takes much more time that updating the database for Debian or Alpine.
Alpine
Gentoo
Debian
Showing available updates
Show which packages have an update available:
Alpine
or:
Gentoo
Debian
Updating a particular package
Alpine
Debian
Gentoo
Installing packages
Alpine
For source compile, see the Aports tree and the abuild tool.
Gentoo
Debian
Debian source compile:
(optional: customize the build by modifying the debian/rules makefile)(or set environmental variables like DEB_BUILD_OPTIONS)(note that this will make your bug reports invalid to the maintainer)
Simplified source compile:
(the packages are automatically generated using the -b switch above)
Note: This process can be used to backport packages from testing and unstable by simply adding their respective source repositories to sources.list, which is similar to adding ~x86 to package.keywords in Gentoo. This is explored further in the 'Architectures and repositories' section below.
Reinstalling a particular package
Alpine
or:
Gentoo
Debian
Note: You rarely need to reinstall a package on Debian
Searching the package database
Alpine
Alpine will only search package names.
Gentoo
To search the package names and descriptions:
Note: On Gentoo, it's actually much better to install and use either the esearch package or the eix package to do a search. You use them like this:
or
Debian
Both emerge and apt-cache search support regular expressions.
To get the long package information on Debian (searching only in package names):
Removing packages
Alpine
apk del will remove configuration files when the --purge flag is used. Make sure you have backups of your configuration files. (Using rcs might be an idea)
You will mostly like to take a quick look at the dependencies before you remove packages recursively.
To see dependencies for a package, use:
To see if package is required by other packages (is a dependency for another packages), use:
Gentoo
Debian
or to remove along with all configuration files
Only downloading packages
This can be useful e.g. if you're on a dial-up connection and want to download everything first and install later.
Alpine
Gentoo

Debian
Cleaning up downloaded packages
Compressed packages that were downloaded for installation can easily consume gigabytes of storage space.
Alpine
Alpine will clean up packages automatically.
Gentoo
To only remove outdated packages you will need to install the gentoolkit package and use eclean:
Cleaning temporary files from emerging packages:
Debian
Only remove outdated packages:
Reverse dependencies
Alpine
apk-tools will take care of reverse dependencies.
Gentoo
Reverse dependencies are a major drawback of Gentoo's current portage implementation: It does not take care of them at all at the moment.If you use the unsafe --unmerge argument, this means that you can uninstall packages needed by others without being warned about it. E.g. you can remove the X server package without portage warning you that KDE (which you have installed as well) depends on it. This way you can actually break your entire system (e.g. by removing glibc).
can fix broken dependencies broken byemerge --depclean
Recent versions of portage include library tracking and preservation with the preserved-libs feature. Portage will notify you to run
emerge @preserved-rebuild
to help rebuild binaries that might otherwise become broken.
Debian
Reverse dependencies are taken care of by dpkg.
Runlevels work pretty conventionally on Debian (see details: systemd). On Alpine and Gentoo, they are a bit different.
Directories and files
In Debian, runlevels are named conventionally (0-6 and S). They are represented by directories in /etc/ called rc*.d (when the default sysv-rc boot loader package is installed; file-rc can be installed instead, and then the relevant file is runlevel.conf).
- /etc/rc0.d
- /etc/rc1.d
- /etc/rcS.d
- /etc/rc2.d
- /etc/rc3.d
- /etc/rc4.d
- /etc/rc5.d
- /etc/rc6.d
In Gentoo, runlevels have the same names, but these are mapped to more self explanatory ones (in /etc/inittab): 'boot', 'default', 'nonetwork', with the option to add more. The directories that represent them are in /etc/runlevels/:
- /etc/runlevels/boot
- /etc/runlevels/default
- /etc/runlevels/nonetwork
In Gentoo, if a service is not explicitly started in a runlevel, it is stopped when switching to that runlevel! There is no explicit stopping of runlevels as in Debian (/etc/rc?.d/K??service).
In both Debian and Gentoo, which things are started (and stopped) in which runlevels is controlled by links in the runlevel directories to scripts in /etc/init.d/, e.g.:Gentoo
Debian
AlpineIn Alpine, runlevels work like they do in Gentoo:
- /etc/runlevels/boot
- /etc/runlevels/default
- /etc/runlevels/sysinit
- /etc/runlevels/nonetwork
- /etc/runlevels/shutdown
Runlevel management
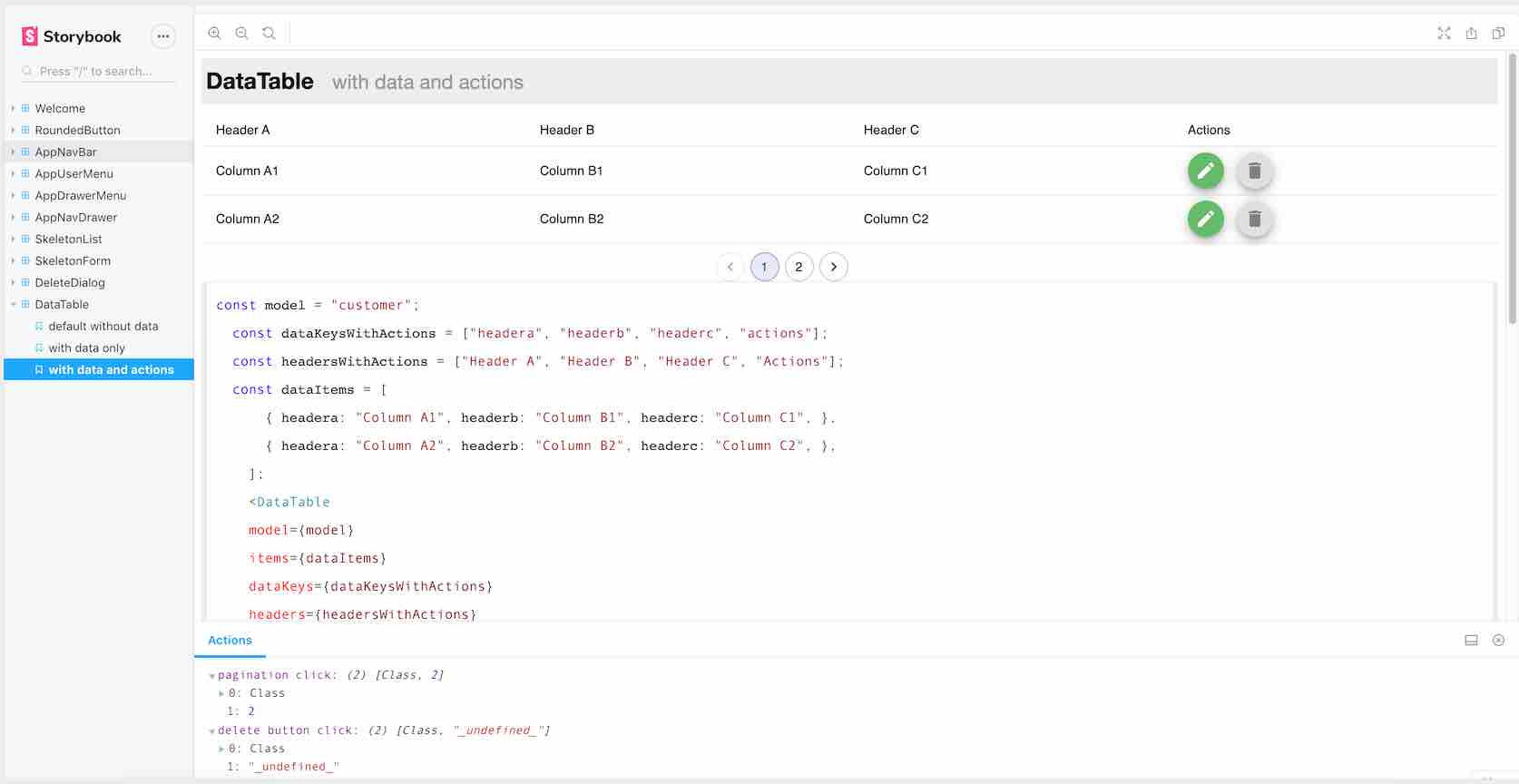
To manage which things to start in which runlevels, use the following commands:
Alpine
To see current status of services in runlevels, do:
To add sshd to default runlevel, do:
The -k option will make sure sshd is stopped when shutting down or reboot.To remove sshd from all runlevels do:
Gentoo
To add the cupsd to the default runlevel, do:
To remove alsasound from the boot runlevel, do:
Also see this wiki page about gentoo runlevel management with rc-update
Debian
Configure cupsd to be started in runlevels 2, 3, 4, 5, and stopped in 0, 1, 6, with sequence code 20:
or simply:
Remove cupsd from all runlevels:
/etc/portage/make.conf and use flags
While in Gentoo there's a large number of configuration files which control the behaviour of the package management system, there are comparatively fewer in Debian, as there is no need to dictate how to compile software which is downloaded and tweak/alter it. In Gentoo, the file /etc/portage/make.conf is used for much configuration; this includes USE flags, which influence which elements of packages are compiled, and which libraries to build support for - common USE flags (USE or -USE to specifically negate support) include 'gtk gnome' for Gnome users (and a corresponding -qt -kde -arts) and 'qt kde arts' for KDE users. A Gentoo user's complete set of use flags may look something like this:
USE='-kde -arts -qt xv truetype bluetooth crypt slang readline gpm berkdb mmx gdbm tcpd pam libwww ssl nls ethereal perl python esd gif imlib sdl oggvorbis mpeg gnome gtk X motif opengl avi png tiff nptl pcmcia nptl ldap eds'
Architectures and repositories
Gentoo
Also in /etc/portage/make.conf is the ACCEPT_KEYWORDS setting, with (for an X86-based processor) two settings, x86 for stabler packages, and ~x86 for bleeding edge packages. It is however not recommended to make this change in /etc/portage/make.conf. Rather configure this per-package in /etc/portage/package.accept_keywords. It's enough to put a line into that file naming the package (for example 'app-foo/bar'). That file might look like this:
The last line says, that only version 4.3-r1 should be unmasked. Older and newer versions will still be ignored.
Note for non-x86 users:The keywords x86 and ~x86 can of course be replaced by sparc and ~sparc for example.
Debian
Setting this in Debian is slightly more complicated, and is accomplished by setting different 'repositories' in /etc/apt/sources.list - along with which 'tree' to use for packages; in Debian, these are stable, testing, and unstable. An /etc/apt/sources.list file for a debian testing user may look something like this:
Alternatively, /etc/apt/sources.list can contain any number of repositories for any trees, and a default tree (this can be overridden using the -t switch on the command line) in /etc/apt/apt.conf:
Per-package settings go in /etc/apt/preferences, somewhat like Gentoo's /etc/portage/package.keywords.
Network
Alpine
Alpine uses /etc/network/interfaces, just like Debian. The main reason is because this is the way busybox does it.
/etc/network/interfaces:
Gentoo
/etc/conf.d/net:
Note that this has changed recently. For more information please refer to http://www.gentoo.org/doc/en/handbook/handbook-x86.xml?part=4
Debian
/etc/network/interfaces:
This chart shows how some standard things are done in Alpine compared to other distributions.
| Action | Alpine (apk) | Arch Linux (pacman) | Gentoo (emerge) | Debian/Ubuntu (aptitute) | Fedora/RHEL/SL/Centos (yum) |
|---|---|---|---|---|---|
| Update package database | apk update | pacman -Sy | emerge --sync | aptitude update | yum update |
| Showing available updates | apk version -l '<' | pacman -Qu | emerge --deep --update --pretend @world | aptitude upgrade --simulate | yum list updates |
| Installing packages | apk add [package name] | pacman -S [package name] | emerge [package name] | aptitude install [package name] | yum install [package name] |
| Update all installed packages | apk upgrade -U -a | pacman -Su | emerge --update --deep @world | aptitude upgrade | yum update |
| Searching package database | apk search -v '[string]*' | pacman -Ss [string] | emerge --search [string] | aptitude search [string] | yum search [string] |
| Removing packages | apk del [package name] | pacman -R [package name] | emerge --depclean [package name] | aptitude remove [package name] | yum remove [package name] |
Squid is a caching proxy for the Web supporting HTTP, HTTPS, FTP, and more. It reduces bandwidth and improves response times by caching and reusing frequently-requested web pages. Squid has extensive access controls and makes a great server accelerator. It is licensed under the GNU GPL.
If you are looking to setup a transparent squid proxy, see this page
- 1Terminology
- 1.2proxy
- 3Basic configuration
- 3.2Testing
- 4SSL interception or SSL bumping
- 4.3Configuration
- 4.3.2Generate cert/key pair
- 4.3Configuration
Terminology
client
A client is often considered a user of a PC or similar system, but more accurately a client is the applications a person uses to access web pages and other resources, and the OS they are running on.
proxy
A proxy is a device which makes connections on behalf of clients. If we consider a common TCP connection, there is one TCP connection between the client (source) and the proxy, and a separate TCP connection between the proxy and the server (destination). Consider this beautiful diagram:
Point A is the client-side connection and point B is the server-side connection.
These are separate, distinct connections, so for example the client-side could be encrypted and the server-side in plaintext (unencrypted), or the client-side could use browser user-agent header x and the server-side connection could use browser user-agent header y.
The proxy is effectively acting as a server to the client, and as a client to the server (OCS). Without a proxy, the connection would simply be from client to server. The destination server is often referred to as the 'OCS' or 'Origin Content Server' - this simply means the server hosting the objects that the client requests (for example the web pages that you want).
The above is of course a simplified version of things. Other factors, such as the HTTP version of the client browser, or existence of the object in cache on the proxy, will have impacts on how many server-side connections are created.
explicit forward proxy
An explicit proxy is one in which the client is explicitly configured to use the proxy, and as such are aware of the existence of the proxy on the network. When the client sends packets to an explicit proxy, they are addressed to the proxy server listening address and port.Squid usually listens for explicit traffic on TCP port 3128 but TCP port 8080 is a common explicit proxy listening port. Explicit proxy deployments are forward proxy deployments, where the clients can make use of the caching and optimisation features of the proxy when making outbound requests. An explicit proxy can be involved in authentication of the client, typically by issuing a 407 HTTP response. Connections to HTTPS sites through an explicit proxy will use the CONNECT HTTP method.This article discusses this type of proxy deployment.
transparent forward proxy
A transparent proxy, also known as an intercepting proxy, does not require any configuration changes on the client, since traffic is transparently sent to the proxy, usually through traffic redirection by a router. When the client sends packets, they are addressed to the destination server. A transparent server can be involved in client authentication; this will usually involve redirecting the client to a virtual domain, typically with a 401 HTTP response.
reverse proxy
A reverse proxy sits in front of a resource such as a web server and answers queries from clients, caching content from the server and optimising connections to it.
cache
A cache is simply an object store. A proxy will usually cache objects (images, html text, downloaded files etc) that are requested by clients, which means storing the objects on the proxy either in RAM or on disk.This has the benefit of a client being able to get the object from the proxy, without having to wait for the proxy to connect out to the destination server (OCS) and download the object again, resulting in a better client experience ('the web pages seem to load faster') and reduced bandwidth (less connections made server side, especially if we consider objects that are repeatedly requested).
Caching is influenced by proxy configuration (what to cache) and by numerous HTTP headers (am I allowed to cache this object? How long should I cache it for?) such as 'Expires', 'Cache Control', 'If-Modified-Since' and 'Last-Modified'.A proxy will usually keep its cache fresh by making requests for cached objects independent of client requests for the objects.
More information
You may also wish to review https://devcentral.f5.com/articles/the-concise-guide-to-proxies which provides further information on various proxy types.
Installation
Install the squid package:
apk add squid
If you wish to use the Alpine Configuration Framework (ACF) front-end for squid, install the acf-squid package:
apk add acf-squid
You can then logon to the device over https://x.x.x.x (replace x.x.x.x with the IP of your server of course) and manage the squid configuration files and stop/start/restart the daemon etc.
Basic configuration
Config file
The main configuration file is /etc/squid/squid.conf. Lines beginning with a '#' are comments.squid should already come with a basic working configuration file but an example configuration file is shown below, which will get you up and running quickly and is well commented but please change the localnet definition for a more restrictive one:
Note:If you change the squid configuration file, you do not need to restart squid in order to load the changes, just use this command instead:
squid -k reconfigure
Testing
Start and check squid
Start the squid service:
rc-service squid start
To start squid automatically at boot:
rc-update add squid
Check the squid configuration for errors:
squid -k check
If there is no feedback, everything is gravy! (that's a good thing).
Check that squid is listening for traffic, using netstat for example:
netstat -tl
You should see a line showing a Local Address and the listening port (in our example config above it is set to 3128). If you don't see this, check the 'http_port' directive is set in the config file and has a value. Ensure this port isn't being used by something else on the system.
Remember to ensure the squid proxy has valid IP configuration including default gateway etc.
Configure the client
Each application using the proxy will have to be configured to send traffic via the proxy. If we assume that our squid proxy is running on IP address 10.0.0.1, port 3128, we would configure the Firefox browser in the following manner:
- Tools>Options>Advanced>Network>Settings...
- Select Manual proxy configuration and tick the 'use this proxy server for all protocols' box
- Under HTTP Proxy: add the squid listening IP address, 10.0.0.1. In the Port: section add the squid listening port 3128
- Click OK to save the changes.
Now browse, you should have internet access, via the proxy!
Many Operating Systems allow a system proxy to be set. Firefox can be set to use the system proxy settings:
- Tools>Options>Advanced>Network>Settings...
- Select Use system proxy settings
- Click OK to save the changes.
The system proxy settings themselves vary from system to system but on an Alpine install you can simply run the setup-proxy script.
It is also possible to configure the browser to use a PAC file. This file is usually hosted on a webserver (which may also be the proxy, but doesn't have to be) and it tells the browser what requests to send to the proxy and which ones to send direct (bypassing the proxy).
The Squid FAQ on configuring browsers offers more information on this topic.
Logs
If you've set the proxy to take access logs, you can view these to see client requests coming in:
tail -f /var/log/squid/access.log
Use Ctrl-C to exit back to the prompt.
SSL interception or SSL bumping
The offical squid documentation appears to prefer the term SSL interception for transparent squid deployments and SSL bumping for explicit proxy deployments. Nonetheless, both environments use the ssl_bump configuration directive (and some others) in /etc/squid/squid.conf for their configuration.In general terminology, SSL interception is generally used to describe both deployments and that will be the term used here. We are, of course, dealing with an explicit forward proxy configuration here.
Behaviour without SSL interception
Clients behind an explicit proxy use the 'CONNECT' HTTP method. The first connection to the proxy port uses HTTP and specifies the destination server (often termed the Origin Content Server, or OCS). After this the proxy simply acts as a tunnel, and blindly proxies the connection without inspecting the traffic.
Behaviour with SSL interception
Using this method, clients still use the CONNECT method. Typically the server-side connection is established first, using the information available in the CONNECT request from the client (such as the destination server and port) which allows Squid to spoof a certificate. The Common Name (CN) will reflect the destination server and the Squid certificate will be used to sign it. This spoofed certificate is then presented to the client when they access a site via the proxy.
Configuration
Add packages
Add the ca-certificates package (required to trust common Certificate Authority (CA) certificates) and the openssl package or libressl package (to create self-signed certificate or CSR). The -U option ensures we update the package list first:
apk -U add ca-certificates libressl
Generate cert/key pair

You obviously don't need to follow both of the next sections. Either generate a self-signed certificate or a CA signed one (you have to pay for the latter) and then amend the squid configuration to enable SSL interception and point it to the key/cert pair generated in these steps.Whether you are using OpenSSL or LibreSSL, the command to use is still 'openssl'.
Generate a self-signed certificate
The following example command will produce a working cert/key pair, saved to /etc/squid/squid.pem:
openssl req -newkey rsa:4096 -x509 -keyout /etc/squid/squid.pem -out /etc/squid/squid.pem -days 365 -nodes
Then adjust permissions:
chmod 400 /etc/squid/squid.pem
In the above example we save the cetificate and key to the same file; they can be saved to separate files if you wish, just adjust paths accordingly.
Generate a CSR to get a CA-signed certificate
Create a private key using the syntax openssl genrsa -out <key_path_and_name> <keysize>
For example:
openssl genrsa -out /etc/squid/squid.key 2048
Create the CSR with the syntax openssl req -new -key <key_path_and_name> -out <csr_path_and_name>
For example:
openssl req -new -key /etc/squid/squid.key -out /etc/squid/squid.csr
You then need to supply the CSR (Certificate Signing Request) to your Certificate Authority (CA). Do not send them, or anyone else, your private key. It should remain private!
Some CA's (such as Thawte and Verisign) provide an online CSR checker, so you can ensure the CSR is valid before providing it to them.
Once the CA receive the CSR and do their thing they should send you back the CA signed public key. Request it in .pem format if possible (it's a widely used standard for certs). You then need to copy this back onto the Squid proxy, to /etc/squid/ if you are following the example here.
Remember to amend the squid configuration to point at the correct locations of the private key and CA signed certificate.
Amend /etc/squid/squid.conf
Next, we need to amend the squid configuration file to use SSL interception. In the below example, we will add a few lines, then amend the http_port directive so that it still serves HTTP requests, but also performs SSL interception on HTTPS connections that are established via the HTTP method CONNECT. You can use a separate http_port for each if you wish, but remember to amend the client configuration to send HTTPS traffic to the alternative port.
The decision you're making with the 'sslproxy_cert_error' (and potentially the 'sslproxy_flags') option is to either close the connection when a certificate error is encountered (such as a self-signed, untrusted certificate is presented), or to pass certificate errors onto the client to allow them to make the choice about the site and whether or not to trust the certificate.
Fix client SSL Warnings
You will need to install the self-signed proxy certificate (in our example we saved it to /etc/squid/squid.pem) to all clients, otherwise they will probably get an SSL error for every domain they visit over HTTPS. It is important to install the certificate as a Certificate Authority (CA) certificate to the client browser for trust to establish properly. If you are using a CA signed certificate (not a self-signed one) then the browser probably already trusts the certificate and so this step will likely not be needed.
For Internet Explorer, you can likely double-click the .pem certificate and use the Certificate Import Wizard to manually install the certificate to the Trusted Root Certification Authorities certificate store.
For Firefox, use Tools>Options>Advanced>Certificates>View Certificates. Under the Authorities tab, use Import... to add the certificate as a trusted authority. Installing the certificate as any other kind of certificate will result in a poor user experience.
Note:If you see the error This certificate is already installed as a certificate authority. be sure to check all locations for existence of the certificate and remove (delete) it wherever found. Firefox likes to install certificates as Server certificates rather than under Authorities as we would like. Once removing all traces of the certificate, please be sure to restart Firefox and try importing the certificate again.
Disable SSL interception for certain sites
Download Git
There may be situations where you wish to disable SSL interception/SSL bumping for certain destinations due to issues with functionality or privacy concerns. As an example, a Windows Dropbox client refused to establish a secure connection because it did not trust the self-signed certificate in use by the proxy. Or, you may wish to allow user privacy to be retained when they are using hotmail.com.In this example we will create an Access Control list (ACL) to prevent SSL interception to *.hotmail.com and *.dropbox.com. Remember that rule order is important, the first match wins! So put more specific rules at the top, more general rules below.
Squid crashes after configuring HTTPS interception
Squid may crash after configuring SSL interception. The service may report as running, but reviewing listening ports no longer shows Squid listening.A review of /var/log/messages may show an error 'The ssl_crtd helpers are crashing too rapidly, need help!'
In this instance, perform the following:
Further reading
Advert blocking
There are several methods to achieve this, you could simply create an ACL for known advert domains (see blocking domains for an indication of how to do this).Another options is to use a hosts file specific to squid (i.e. unrelated to the system hosts file), which will direct traffic for known adverts/malware sites to the localhost. The connection can then either fail (because there is no web server running at 127.0.0.1:80 to service the requests that are redirected by the hosts file to localhost) and squid will display a standard error, or you can have a web server running that will respond with some form of 'advert blocked' page.
Blocking ads will save bandwidth and should improve page load times. As a drawback, some pages may look untidy or odd without advertising in place.
The first thing to do is either create a hosts file yourself or find a pre-configured one such as this one (note that this file is free to use for personal use only, see the full license here.
Whichever method you choose, save the hosts file to the local filesystem, in our example to /etc/squid/hosts.txt
Then, add the hosts_file directive to the squid configuration:
Remember to reload the configuration/restart the squid service for the changes to take effect.
Blocking domains
If you have a large number of domains you wish to block, instead of adding them directly to the squid configuration file the best option is to create a separate list and reference this in the configuration file.The domain list should have domains listed one per line. There is an example list (warning, this doesn't get updated!) available here We will refer to this list in our example below.
- Create your own, or download a domain list and save it to /etc/squid/porndomains.acl:
- Amend the squid configuration file at /etc/squid/squid.conf as follows:
- Check the squid configuration for errors:
squid -k check
and if there are none, apply the changes:
squid -k reconfigure
Alpine Install Git Package
- Done! Domains from the list should now be blocked.
You can of course create your own lists of domains and add blacklists/whitelists to your configuration based on the above example. Each list should of course have a unique name.
DNS configuration
Alpine Install Git Block
No additional DNS configuration is required since by default Squid will use the settings in /etc/resolv.conf.You may wish to change this behaviour for your environment or tweak settings to improve performance, as per the below example. It's heavily commented as always for my examples, change to suit your needs.
Install Git Linux
More information
Alpine Install Git Command
